HOW TO SOLVE THE HACK THE BOX INVITE CHALLENGE
Hack the box is an interesting site for both beginners and advanced hackers/ info sec enthusiasts. It is basically a site to practice and perfect your skills.
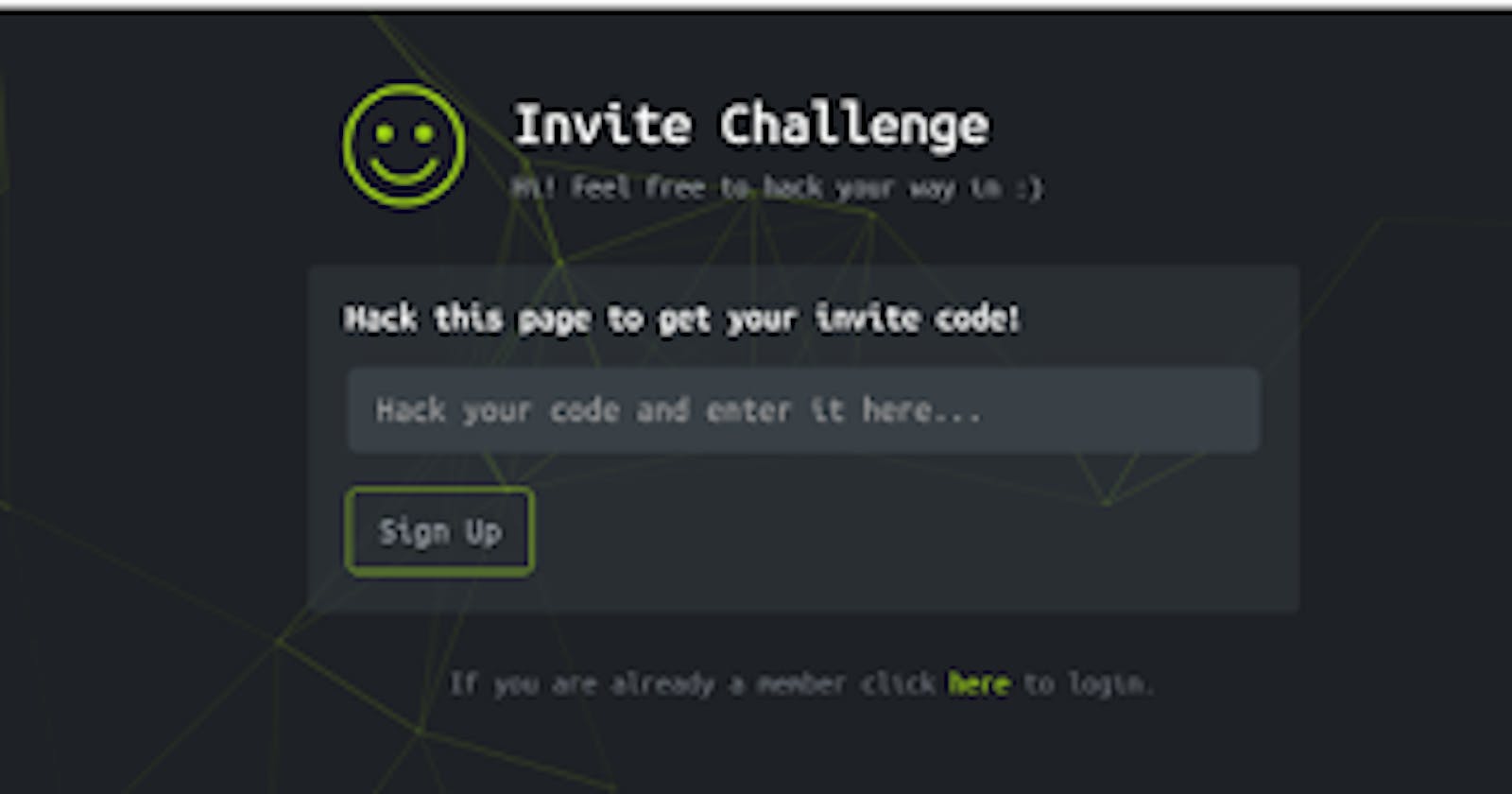
And the most interesting part is not everyone can get in! That's right, hack the box has a "sign in" challenge. You basically have you hack your way in 😓😓.

So in this blog post, I am going to show you how I solved the sign-in challenge, even though there are probably other ways to solve it (maybe even shorter or easier methods)
The invite link is here
The first thing that comes to my mind is developer tools (right-click on the page and choose inspect element). So I look through it but can't find anything particularly interesting. So I click on the hint button.
The hint says we should check the console. So that's where I go.
In the console, we see this weird-looking skull (lol). But under we see another hint that says something about a weird js script that the page loads.

So we simply have to find the said js file, I check a few until I come across this one invite.min.js, When I check it out, it looks unreadable. There are ways to make it readable but I quickly noticed in this case it was not necessary. Because I notice an interesting js function called makeInviteCode.
So I go to the console and run the function
It returns a value but it looks encoded, and I can identify it as base64 because it is a multiple of 4 and it is made up of characters from A-Z and 0-9 (You get the idea)
So I have to decode the message. After decoding (using any online base64 decoder), we are asked to make a POST request to api/invite/generate. I tried making the request with curl but it was just giving weird results. Recaptcha was probably messing with it. So I make the request on the console using the fetch() function.
fetch('/api/invite/generate',{
method: "POST"
})
.then(response=>response.json())
.then(data=>console.log(data))
Apparently this doesn't work on firefox (or maybe I'm just too dumb to see why). So I check chrome and it works perfectly
We can see the data is still encoded in base64, so we decode again.This time using the atob() function on the console And it now looks like an invite code (hopefully).
copy and paste and we're in...Well that was fun
PS: This post was originally published on 9-04-2021 on Blogspot. Therefore the solution given here is as is obtainable in the invite challenge in 2021.